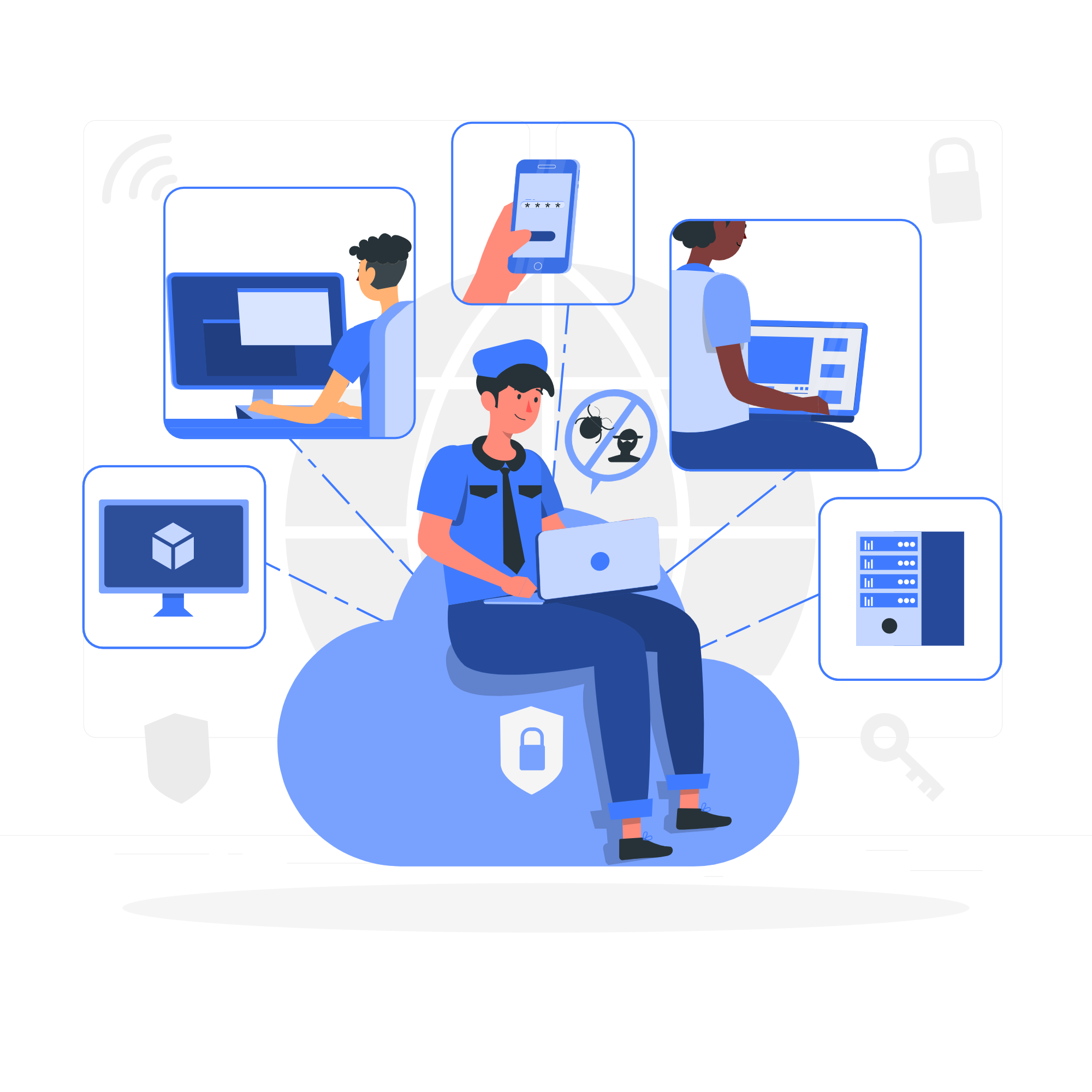
Why is cybersecurity important?
Antivirus programs and firewalls are no longer effective at stopping cyber threats. Cyberattack risk is continually rising,
and for businesses and institutions, the question is no longer "if," but rather "when.".This is why cyber security is so important.
A solid cybersecurity plan can give users and organizations a good security posture
against malicious assaults intended to gain access to, alter, delete, destroy, or extort sensitive data and systems.
A system's or device's activities being disabled or otherwise disrupted can be prevented with the help of cybersecurity.